 With supply chain attacks surging, now is the time to reflect — and look forward. ReversingLabs’ new report explores trends, best practices and more.
With supply chain attacks surging, now is the time to reflect — and look forward. ReversingLabs’ new report explores trends, best practices and more.
Software supply chain attacks have moved from the periphery to the center of conversations about cyber risk and cybersecurity in recent years. SolarWinds, a substantial December, 2020 software supply chain attack that affected more than 18,000 customers and led to breaches at hundreds of organizations had a lot to do with that -forcing industry and regulators to take a hard look at software supply chain risk.
So where do things stand in 2022? And what can we expect to see in 2023? Our new report: The State of Software Supply Chain Security 2022-23, attempts to answer those questions: summarizing 2022’s biggest trends and exploring what's in store for software supply chain security in 2023. Here are the key takeaways.
1. Software supply chain attacks are surging
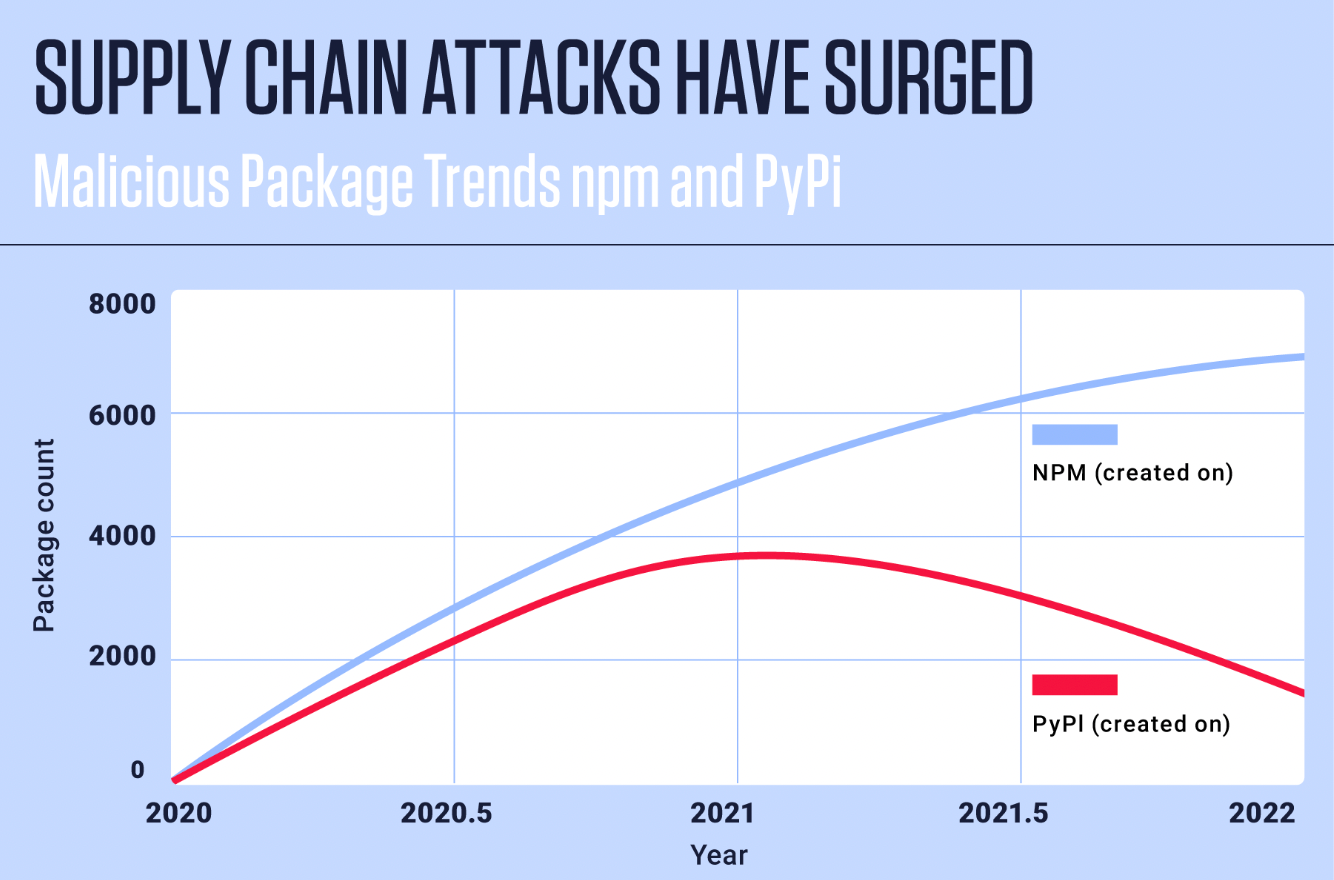
It should not come as a surprise that software supply chain attacks have grown in number over the past year, as open-source software repositories have become a favored avenue of attack for cybercriminals. According to ReversingLabs’ 2022 NVD Analysis, attacks on popular repositories, specifically npm and PyPI, have spiked by 289% in the last four years combined.
ReversingLabs threat researchers have seen these attacks first-hand as well, with the discoveries of attacks such as IconBurst and Material Tailwind, demonstrating that malicious actors are taking advantage of the industry’s trust in open source software repositories. Threat actors do this by implanting malicious code that is then amplified by the repositories, extending the reach of attacks.
ReversingLabs new report found that the biggest playground for malicious actors is the popular JavaScript repository npm, with the number of malicious npm packages jumping by more than 40% this year. The reason for this is easy to understand: compared to PyPI and RubyGems, npm hosts far more code - and thus far more attacks on that code. Specifically: ReversingLabs researchers found that nearly 7,000 malicious packages were added to npm, making it a cybercriminal’s target of choice.
2. Multiple supply chain threats are on the table
Not only have attacks on open-source software repositories like npm increased over the past year, but attack methods have continued to evolve and exploit organizational mistakes.
A popular attack method showcasing malicious intent is typosquatting, which was employed in both the Material Tailwind and IconBurst supply chain attacks discovered by ReversingLabs. By creating look-alike packages with names that mimic popular software packages, malicious actors are able to trick developers into downloading a malicious package, rather than the legitimate one. Though they are passive attacks, typosquatting can be very effective at pushing malicious code to unwitting development projects. In the IconBurst attack, for example, the icon-package typosquatted module was downloaded over 17,000 times before being removed from npm.
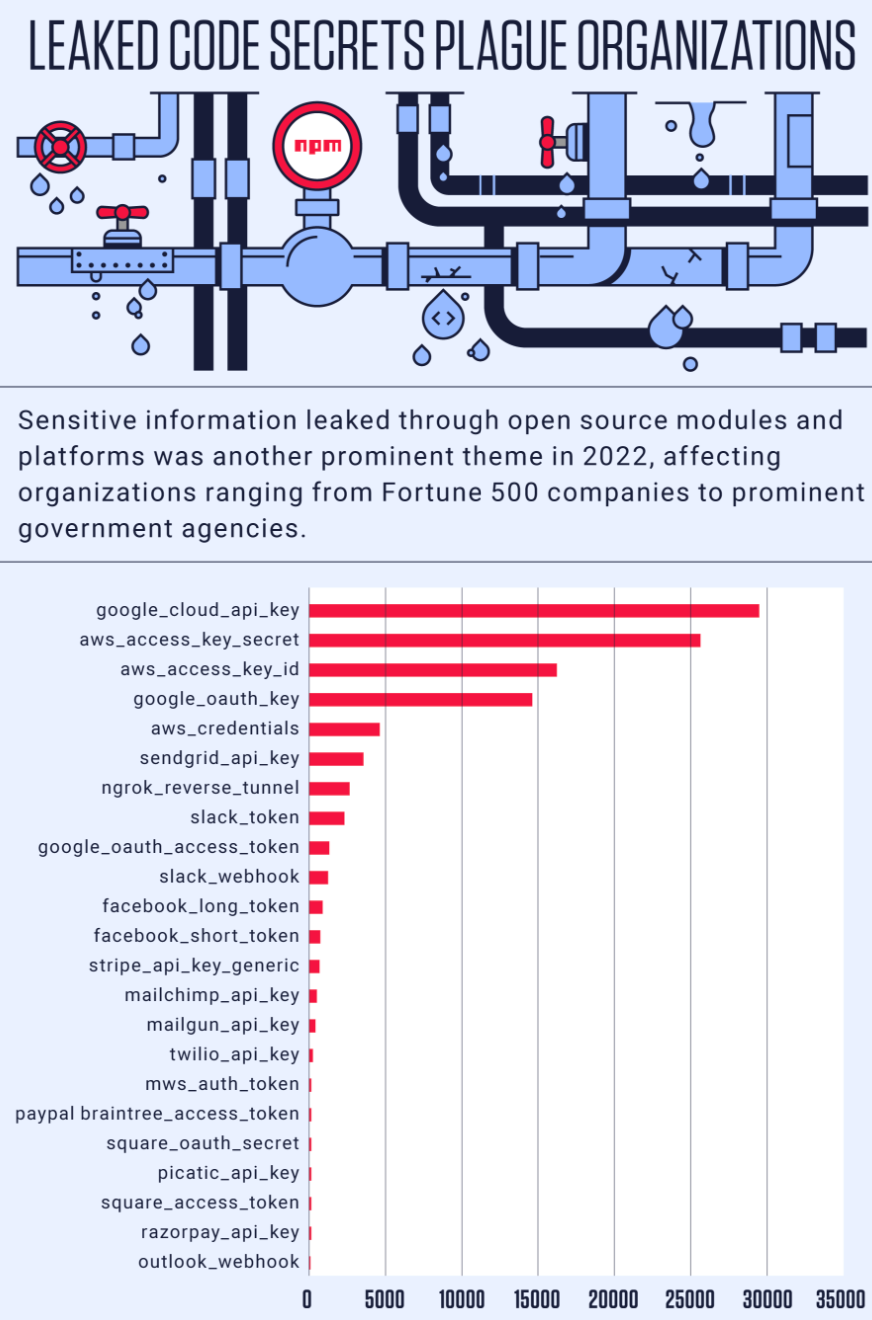
Secrets leaks — when an organization leaves sensitive information in public source code — are another example of how a glanced-over mistake can be taken advantage of by cybercriminals. The U.S. Department of Veterans Affairs and Toyota both suffered secrets leaks in 2022, showcasing that both private and public entities are not actively monitoring for leaked secrets on open source repositories.
The State of Supply Chain Security 2022-23 makes the case for a shift in how we use and rely on open source repositories, one that includes increased security and scrutiny of the code hosted on these platforms.
"We've seen malicious attackers turning their attention to the software supply chain as they recognize source code as an abundant source of unintentionally embedded secrets, which can be used to further attacks."
—Charlie Jones, Evangelist, ReversingLabs
3. 2022 is the wake up call, so take action in 2023
Based on the numbers from the past couple of years, software supply chain attacks will continue to be robust in 2023. But the vast increase in these attacks also makes it likely that organizations will be more prepared than ever before to defend against and prepare for these kinds of threats.
Top 5 predictions
-
1. Software supply chain attacks will accelerate
-
ReversingLabs’s new report argues that the number of software supply chain attacks will continue to grow in a steady, linear fashion, as has been the case this past year (with some exceptions).
-
2. Software platform owners will boost defenses
This past year, platforms such as GitHub and PyPI took steps to improve security. ReversingLabs expects that improvements such as malicious package detection, integrated password-reuse checks, and more will be added to these platforms in 2023.
-
3. Software supply chain security automation will take hold
-
The constantly increasing pace of software development is outrunning security measures that need to be taken to minimize threats. In order to keep up, ReversingLabs believes that automation will become more widely adopted to aid this problem.
-
4. Federal guidance will start to bite
-
Mandates for federal government software vendors are coming, with compliance deadlines in 2023. Also, more policy addressing software security is under way.
-
5. More organizations will dedicate time and resources to open source software
-
As a result of the various software supply chain attacks based in open source repositories, more organizations will dedicate their time and resources to combatting the risks associated with these repositories.
Get ahead of supply chain risk in 2023
Download The State of Software Supply Chain Security 2022-23 to gain a deep understanding of:
- Key trends in software supply chain security
- How and where supply chain threats are concentrated
- New federal mandates for supply chain security (EO 14028 etc.)
- Emerging best practices to get ahead of supply chain risk in 2023
- Key steps to start your software supply chain security program



