July 14, 2022
Experts say we need new key-exchange and signature algorithms, to resist attacks from quantum computing. Orgs have had a go, but now NIST has weighed in.
July 12, 2022
ReversingLabs researchers uncovered a campaign to install malicious NPM modules harvesting sensitive data from forms embedded in mobile apps and websites.
July 7, 2022
It’s a truism often repeated: Don’t roll your own cryptography! The Police CyberAlarm service deftly shows why.
July 6, 2022
Container adoption is ramping up. With software supply chain attacks also on the rise, you need to expand your software security approach. Here's how.
June 30, 2022
Should you use GitHub Copilot? “No,” say open-source fans. “Heck no,” say lawyers. “Yeah,” say the sort of devs who do Stack Exchange copypasta.
June 29, 2022
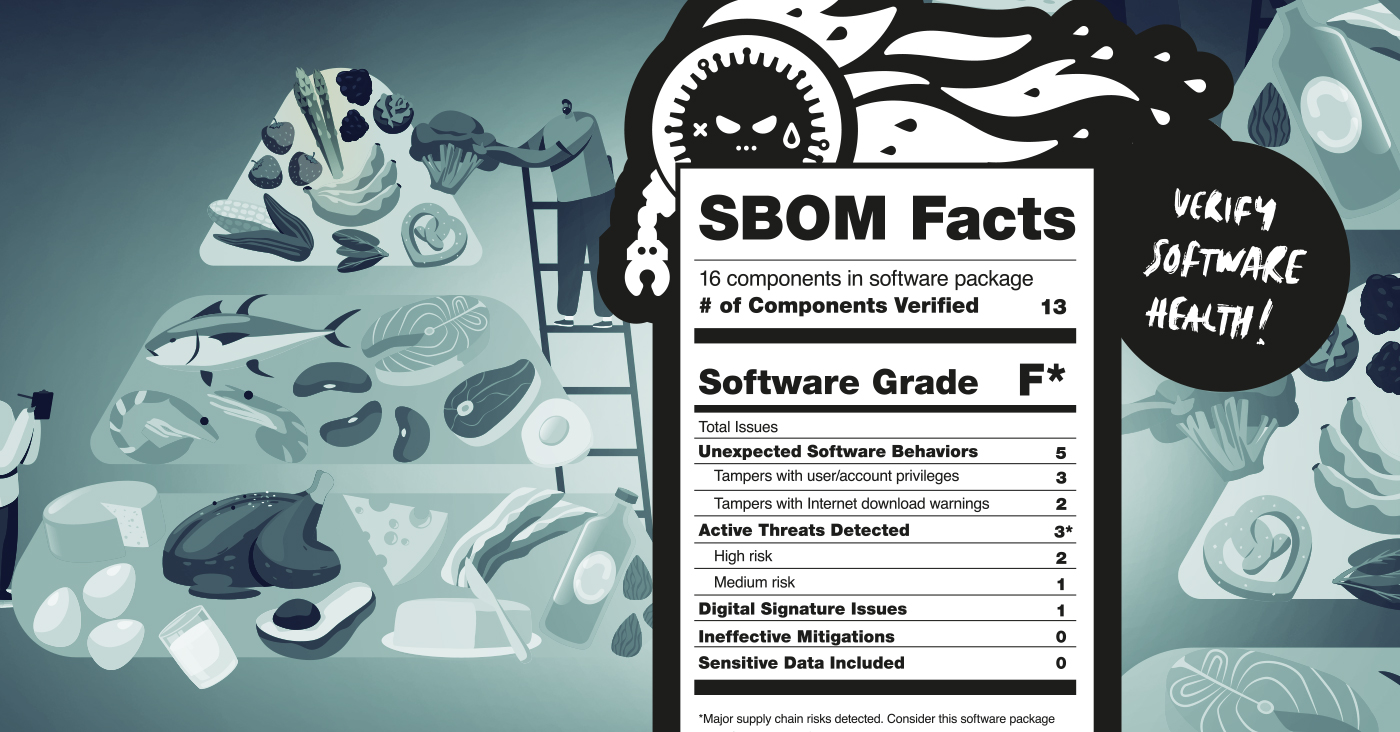
Not knowing what’s in your food can have consequences. The same is true for software. You need a software bill of materials (SBOM) to minimize risk.