
Operation ShadowHammer is a new and highly targeted software supply chain attack discovered by Kaspersky Lab. The attack leveraged ASUS Live Update software to distribute malicious code. Live Update is a utility which commonly comes pre-installed on most ASUS computers and is used to update system drivers and BIOS/UEFI code.
As the details of this supply chain attack are still unfolding our ReversingLabs researchers looked into what is currently publicly available. Using our Titanium Platform we’ve been able to make a few connections which lead us to, what we believe is, the first iteration of this malware code.
We started from the infected installation package that was published by Kaspersky Lab. Its content is the main installation file called Setup.exe and two additional MSI installation packages that contain all the software components that get installed on the system.
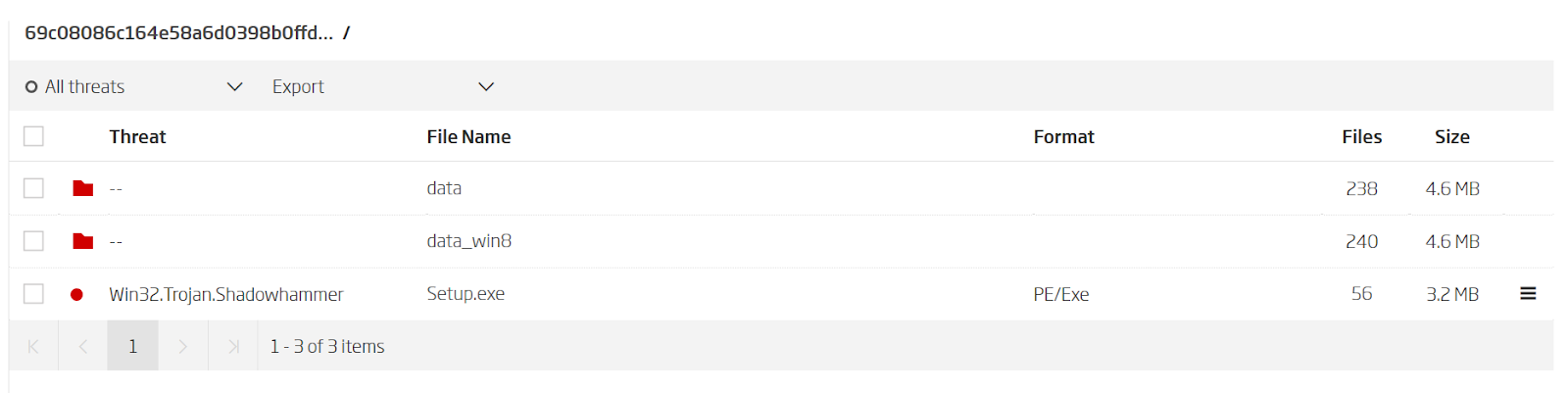 Infected ASUS installation package - courtesy of Kaspersky Labs
Infected ASUS installation package - courtesy of Kaspersky Labs
The main executable file, Setup.exe, carries the malicious payload. Because of this, we decided to take a look at how we could pivot around Setup.exe and find additional samples to analyze. Using our RHA1 functional similarity algorithm we’ve been able to do just that and find 10 additional samples worth taking a closer look at.
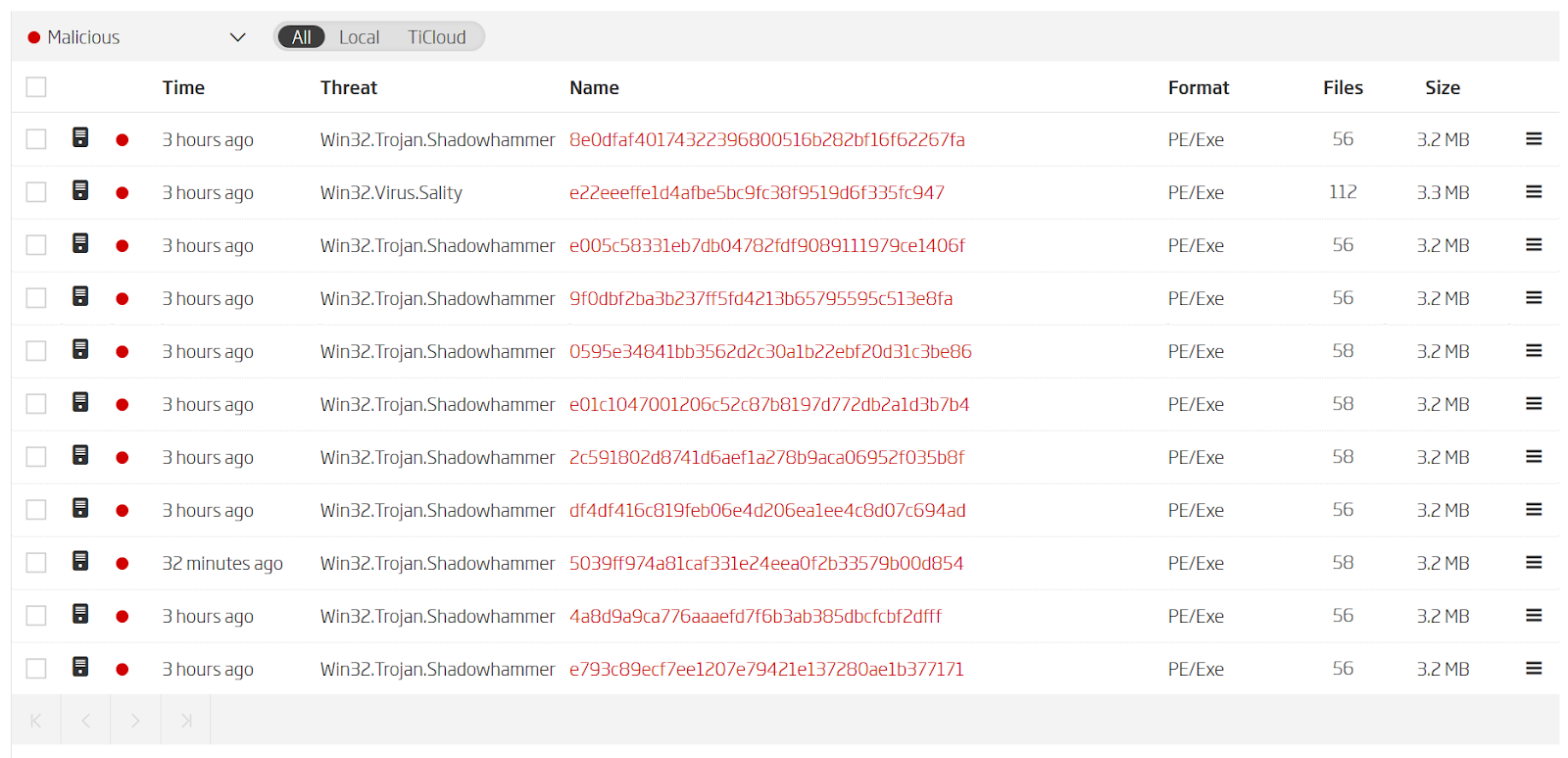
Pivoting to find similar files via ReversingLabs RHA1 functional similarity algorithm
From this point, the investigation is carried forward by TitaniumCore, our advanced file decomposition engine. TitaniumCore has been able to extract embedded resources from all of the RHA1 detected installation packages. The installation packages which have 58 extracted files are particularly interesting as they contain one variant of the ShadowHammer attack.
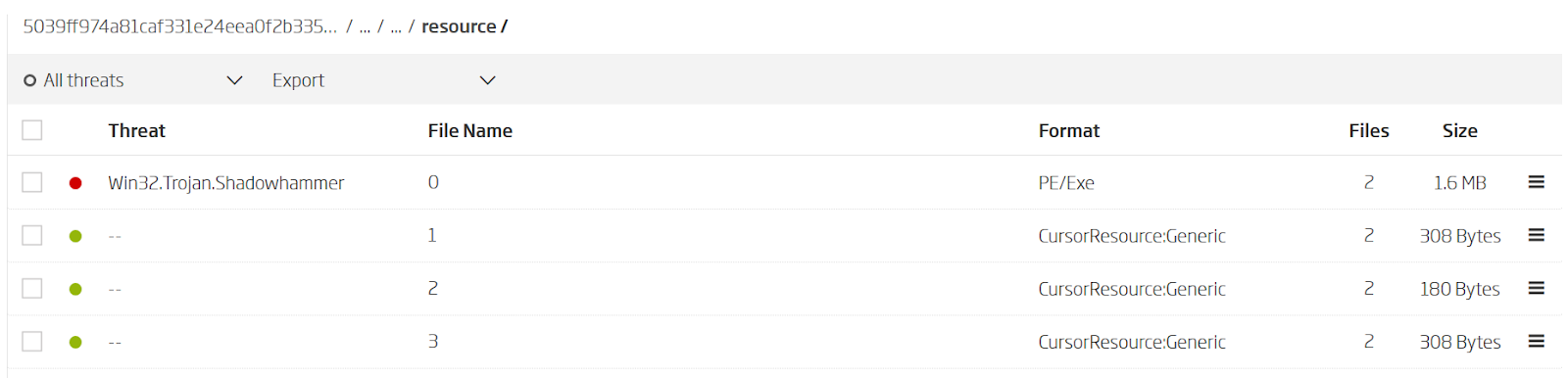
Extracted resources via ReversingLabs TitaniumCore static unpacking engine
This extracted executable is a Visual Studio C++ application that has been compiled with debug symbol information enabled. These symbols unveil a bit more about the attacker and the attack timeline.
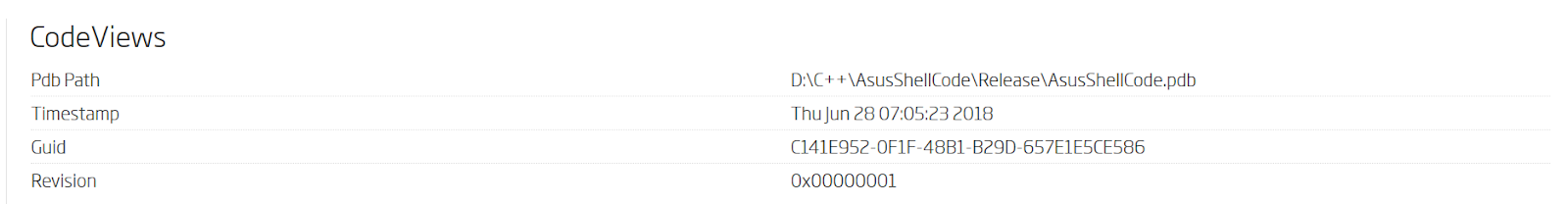 PDB debugging information found within the extracted executable file
PDB debugging information found within the extracted executable file
Based on the specifics of the file path, we were able to conclude that this is the original code the adversaries developed specifically to carry out this attack. Since PDB paths are indexed by our advanced search capabilities, finding all the other samples that share this path, requires only a simple one keyword search.
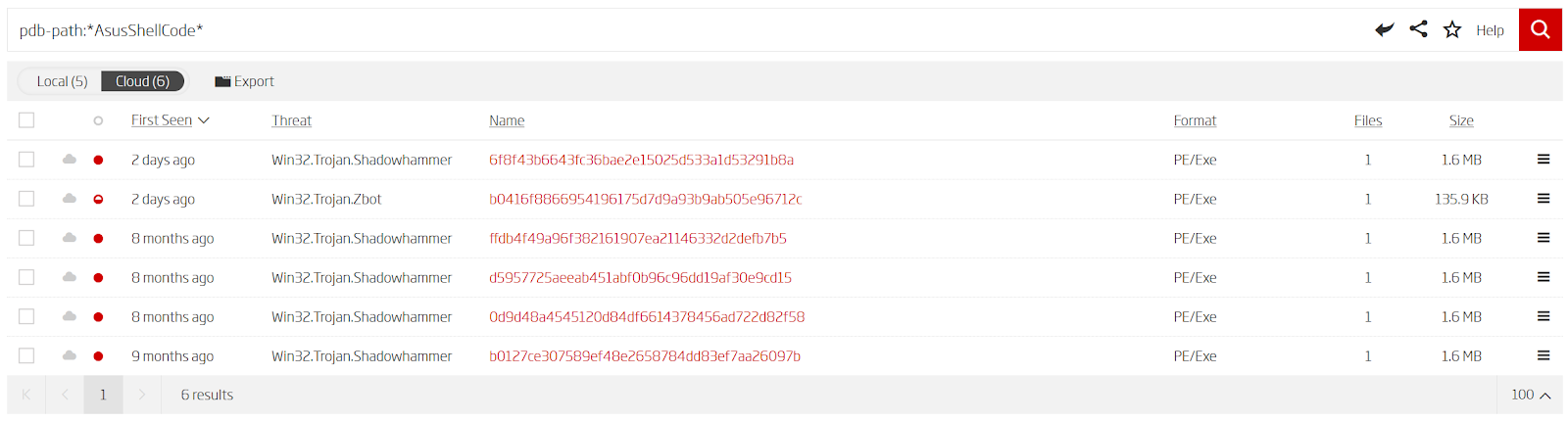
Pivoting to other versions of the same malware via ReversingLabs Advanced Search
Within this batch of samples, we looked at the oldest one, which has the following debugging information.
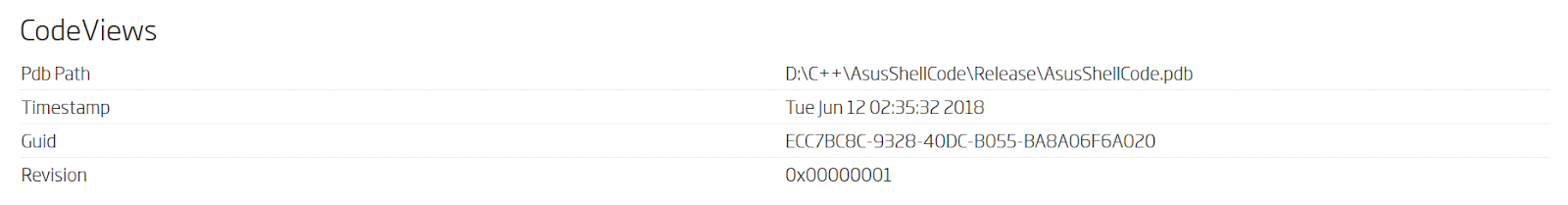 PDB debugging information found within the extracted executable file
PDB debugging information found within the extracted executable file
The timestamp information within aligns perfectly with the attack timeline described by Kaspersky Lab.
The details of the attack are still being investigated by our own team and the teams of security researchers around the world. Our hope is that this short threat hunting blog will help those looking for more details as they put the pieces of this puzzle back together.
IOCs:
1bb53937fa4cba70f61dc53f85e4e25551bc811bf9821fc47d25de1be9fd286a
682fc8ccfc9316c54f02ae7865eee553ad0211031d4d80bb9c4365fbbc74049a
9acd43af36f2d38077258cb2ace42d6737b43be499367e90037f4605318325f8
6edc5578d824f42a6dd34664284179060f5595310fcb437a184f1ac0fc4fb1b4
cfbec77180bd67cceb2e17e64f8a8beec5e8875f47c41936b67a60093e07fcfd
c299b6dd210ab5779f3abd9d10544f9cae31cd5c6afc92c0fc16c8f43def7596


