Carolynn van Arsdale

Writer, ReversingLabs. Carolynn is a reporter, writer, and researcher in the cybersecurity space. She has written for several publications, such as The Security Ledger and Security Boulevard. She has been involved in podcast and event production, and now produces ConversingLabs, a ReversingLabs podcast. Prior to joining ReversingLabs, Carolynn held communication roles in the non-profit and higher education spaces. Her official title at ReversingLabs is Manager, Content Marketing.
Recent Posts from Carolynn van Arsdale
December 7, 2022
With supply chain attacks surging, now is the time to reflect — and look forward. ReversingLabs’ new report explores trends, best practices and more.
December 1, 2022
One year ago, a vulnerability in Apache’s Log4j turned the security world on its ear. What has changed since then? Here are the key takeaways from Log4Shell's legacy.
November 2, 2022
Security operations centers (SOCs) and developers need to share the responsibility for securing the software supply chain. Find out why in ReversingLabs' latest report.
October 17, 2022
MITRE's software supply chain security summit highlighted software companies and government agree that SBOMs are essential.
June 29, 2022
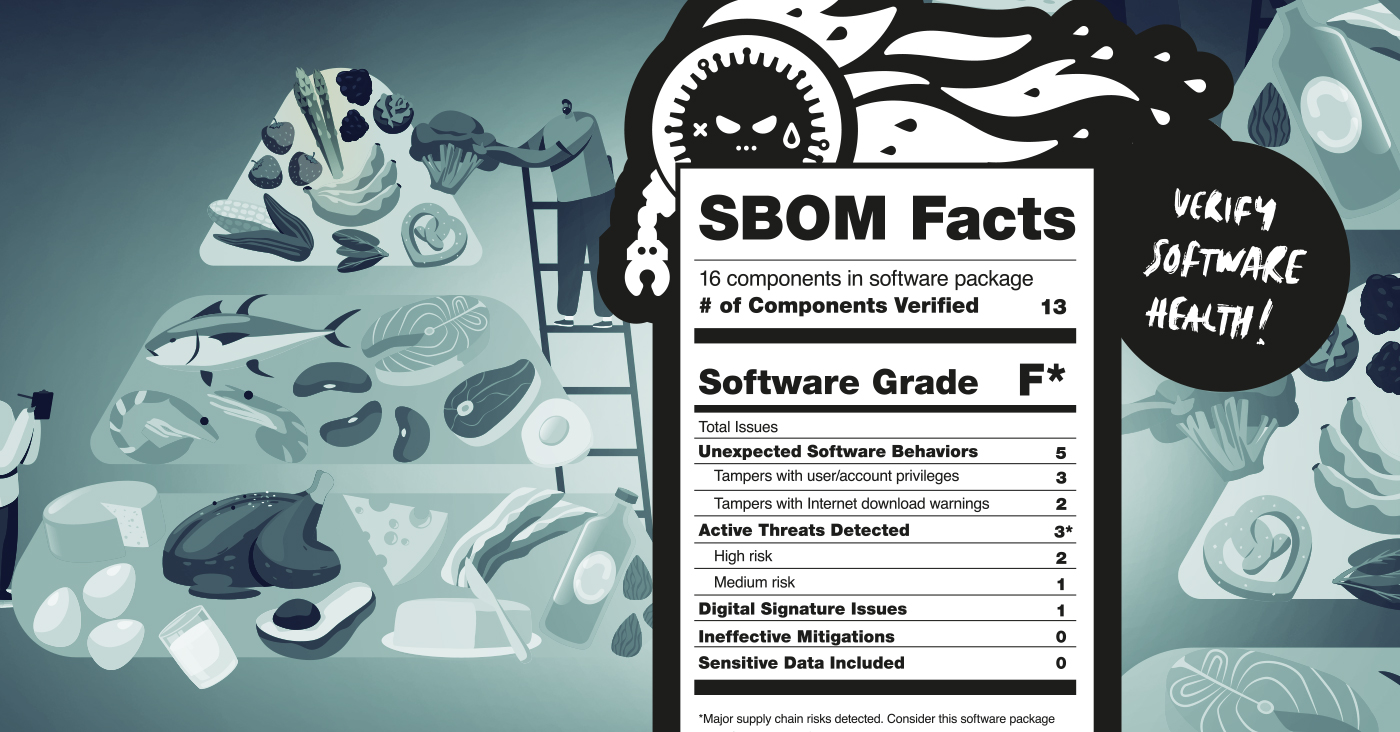
Not knowing what’s in your food can have consequences. The same is true for software. You need a software bill of materials (SBOM) to minimize risk.
June 23, 2022
A survey of more than 300 software professionals found the threat of supply chain attacks looms large—but efforts to detect and block them lacking.